Annonymous Hackers Group Revolutionizing Digital Financial Asset Security
The emergence of the Anonymous Hackers Group has captivated the imagination of many with its unparalleled expertise in the world of cybercrime. Hacking and recovery of digital financial assets, exploring their role in safeguarding vital elements such as cryptocurrencies, credit cards, bank accounts, and mobile payments. Join us as we uncover the innovative hacking software tools for iOS, Android, and Windows that have become the signatures of this mysterious group. Hire a hacker, Hire a Crypto Recovery Service, recover scammed bitcoin, Crypto recovery Agency for Hire, bitcoin core passphrase recovery
The Art of Hacking and the Vulnerability of Crypto Assets
USDT
USDT (Tether), the popular dollar-pegged stablecoin, has gained significant traction in the crypto market – and likewise, hackers have taken notice. We discuss the challenges of recovering lost or stolen USDT and delve into the efforts made by crypto exchanges and blockchain forensic experts to curb this alarming trend.
Ethereum and NFTs
Ethereum is the go-to blockchain for smart contracts and decentralized applications, but it too falls victim to hacking. In this section, we explore the valuation of stolen ETH and delve into the intriguing world of NFTs, where stolen digital collectible assets become serialized and traceable.
Bitcoin (BTC)
Hacking has acquired a notorious reputation, and unfortunately, it extends to the realm of cryptocurrencies. As the value of crypto assets continues to soar, hackers are increasingly targeting individuals and crypto-related platforms.

Recovering Your Crypto Assets From Hackers and Recovering Lost Investments on Trading Platforms
Hacking and recovery of lost or stolen crypto assets on popular platforms like Binance, Trust Wallet, Metamask – NFT, Bitcoincore, Blockchain, and Coinbase. Hire a Crypto Recovery Service, recover scammed bitcoin, Crypto recovery Agency for Hire, bitcoin core passphrase recovery, Hire a hacker
We are able to recover lost assets/ Accounts understanding the vulnerabilities specific to trading platforms like Binance, Trust Wallet, Metamask – NFT, Bitcoincore, Blockchain, and Coinbase.
Binance
– Explore Binance’s robust security features that make it one of the most secure trading platforms in the market.
– Understand the measures taken by Binance to prevent hacking attempts and protect its users’ funds.
– Learn about the recovery options available for users who have lost their assets due to hacks or scams. Hire a hacker
Trust Wallet and Metamask – NFT
– Examine the security features of Trust Wallet and Metamask – NFT, two popular wallets used for non-fungible tokens (NFTs).
– Discover the tools and practices to safeguard your NFT investments against potential hackings.
– Understand the steps to retrieve lost or stolen NFT assets on these platforms.
Bitcoincore and Blockchain
– Delve into the security measures adopted by Bitcoincore and Blockchain, two widely used platforms for Bitcoin transactions.
– Explore the intricate process of recovering lost or stolen Bitcoin assets.
– Learn about additional security measures you can implement to protect your Bitcoin investments.
Coinbase
– Understand Coinbase’s security protocols that provide a top-tier defense against hacking attempts.
– Discover the various methods employed by Coinbase to ensure the safety of users’ crypto assets.
– Explore the possibilities for recovering lost or stolen funds on Coinbase.
Hire a hacker Hire a Crypto Recovery Service, recover scammed bitcoin, Crypto recovery Agency for Hire, bitcoin core passphrase recovery

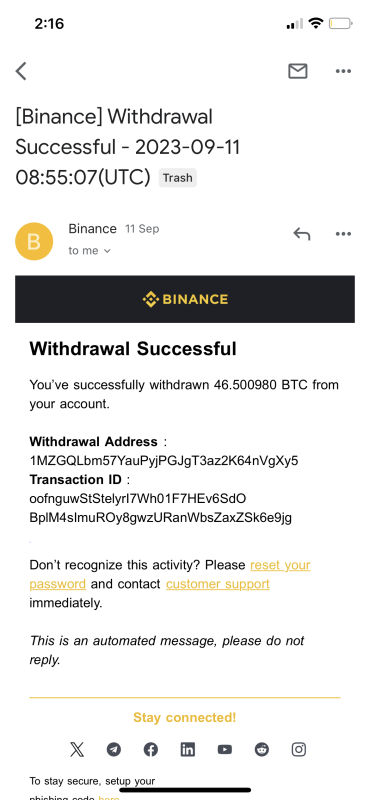

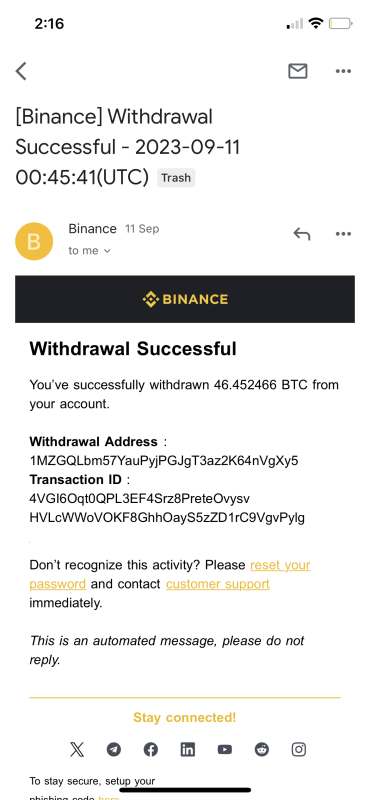
Ethical Hacking vs. Unethical Exploitation
– Draw a clear line between ethical hacking and malicious exploitation of computer systems.
– Emphasize the importance of responsible hacking practices and the legal implications of crossing ethical boundaries.
– Provide tips and resources for readers interested in pursuing a career in ethical hacking and data recovery.
– Delve into the concept of hacking and data recovery, emphasizing their importance in today’s tech-savvy world.
– Recognize the different scenarios where hacking or data recovery may be necessary.
– Highlight the common myths and misconceptions associated with hacking.
Reporting Credit Card Fraud and Recovery
Understanding the appropriate channels to report credit card fraud is vital in the recovery process. This section will provide individuals with step-by-step guidance on the necessary actions to take when their credit card information has been compromised. Facilitating effective communication with credit card companies ensures a swift resolution and maximizes the chances of recovery.


The Crypto Quandary: Tracing the Untraceable
Bitcoin, the undisputed king of cryptocurrencies, is often at the forefront of hacking incidents. But what makes Bitcoin so alluring to hackers, and is there a chance to recover stolen BTC? We unpack the complexities of tracing Bitcoin transactions and explore potential solutions to mitigate the damage caused by its illicit usage.Hire a hacker Hire a Crypto Recovery Service, recover scammed bitcoin, Crypto recovery Agency for Hire, bitcoin core passphrase recovery
Cypto recovery expert
Hack Computer System: Unraveling the Intricacies of Mac OS, Windows OS, and Linux OS
Delve into the world of computer hacking as we explore the ingenious methods employed by attackers to breach the defenses of Mac OS, Windows OS, and Linux OS. Gain an understanding of the techniques hackers utilize to exploit security deficiencies, including phishing, keylogging, and remote access tools. Discover the critical steps one must undertake to secure their computer systems, safeguard sensitive data, and minimize potential hacking risks. Furthermore, uncover the secrets of data recovery when faced with a compromised computer system.

Mac OS
– Explore the unique features of Mac OS and its security measures against hacking attempts.
– Provide an in-depth guide to hacking a Mac system for data recovery purposes in case of emergencies.
– Highlight the best tools and software specifically designed for Mac OS data recovery.
Windows OS
– Discuss the prevalence of Windows OS and the potential security risks it faces.
– Showcase effective techniques to hack a Windows system, ensuring the successful retrieval of lost data.
– Review the top-rated Windows OS data recovery software available in the market.
Hire a hacker
Linux OS
– Shed light on the lesser-known Linux OS, its intriguing security architecture, and the potential for data recovery.
– Highlight the distinctive features of hacking a Linux system and the ethical considerations involved.
– Discuss the available options and tools for data recovery in a Linux environment.
Hack Mobile Phone: Unlocking the Secrets of iOS and Android OS
When it comes to mobile devices, hacking methodologies significantly differ depending on the operating system. Discover the latest techniques used by hackers to gain unauthorized access into iOS and Android devices, providing crucial insights to thwart potential attacks. From social engineering tactics to exploiting vulnerabilities, learn how hackers capitalize on security loopholes. Additionally, explore essential measures to protect your Android or iOS device against unauthorized access and employ recovery techniques when data is lost
hacking tools

Title: Safeguarding Your Finances: Hacking and Recovery of Financial Assets
Hacking and Recovery of Bank Accounts:
Recovering hacked bank accounts involves a combination of swift action, cooperation with financial institutions, and meticulous documentation. This section will delve into the specific steps individuals can take to reclaim control of their compromised accounts and restore financial security gradually
Taking Back What’s Yours:
If you fall victim to hacking or your financial assets are lost or stolen, don’t panic.
Hacking and recovery of lost/stolen financial assets from popular mobile payment apps such as Cash App, Zelle, PayPal, Venmo, Apple Pay, Google Pay, and Facebook Pay.

Hacking and Recovery of Lost/Stolen Financial Assets
Mobile Payment Apps, Cash App, Zelle, PayPal, Venmo, Apple Pay, Google Pay, Facebook
Hacking and Recovering Lost or Stolen Crypto Assets
In the evolving world of cryptocurrencies, the secure storage and protection of your digital assets have become paramount. However, despite the advancements in security measures, hacking incidents leading to the loss or theft of crypto assets are still distressingly prevalent. In this blog post, we explore the realm of hacking and the potential avenues for recovering lost or stolen crypto assets, (BTC), USDT, Ethereum (ETH), (NFTs).Hire a hacker Hire a Crypto Recovery Service, recover scammed bitcoin, Crypto recovery Agency for Hire, bitcoin core passphrase recovery. Recover Scammed USDT

Unveiling the Art of Hacking and Recovering Lost Mobile Phone and PC Data
While hacking might be seen as a dark art, data recovery acts as a ray of hope, allowing users to retrieve vital information lost due to various circumstances. Learn about cutting-edge data recovery techniques capable of resurrecting deleted files, damaged partitions, and corrupted storage systems. Uncover the tools and software available to recover lost mobile phone data, regardless of the operating system, and understand the methodologies deployed in PC data recovery across diverse OS platforms.

In today’s digital age, our mobile phones and PCs have become an integral part of our daily lives, encompassing both personal and professional aspects. However, the risk of losing valuable data due to accidental deletion or theft cannot be ignored. This is where hacking and data recovery techniques play a vital role. we explore some clever ways to hack computer systems and recover lost data, focusing on the three major operating systems: Mac OS, Windows OS, and Linux OS. So, fasten your seatbelts, as we unlock the secrets to safeguarding and retrieving your precious digital memories!

